This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
How to Enable MFA for Your SonicWall Firewall

I have illustrated time and time again that MFA should no longer be considered a nice to have but a requirement when securing cloud services for your organization. Here are a few blogs I have written regarding that topic:
- Why Do I Need Multifactor Authentication in Office 365? Isn’t a Password Enough?
- Microsoft MFA Update
Now that you have seen the security improvements from requiring MFA for Microsoft 365 services like Outlook, Teams, SharePoint, etc., you are now looking for additional easy wins for MFA in your existing infrastructure. One such way is by enabling MFA for users authenticating via VPN. Today’s blog will illustrate how to enable MFA with a SonicWall firewall using built-in users simply for the sake of ease of demonstration.
Step 1: Configure mail server settings
In version 6.5 of the SonicWall OS, this setting is in Manage > Logs & Reporting > Log Settings > Automation > Mail Server Settings.
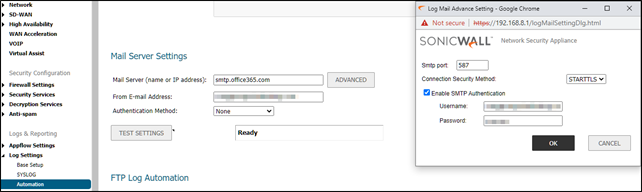
Here I have the mail server defined as Office 365’s SMTP address of smtp.office365.com. Clicking the advanced button gives you the option to choose the port, security method and to provide the credentials to connect.
Step 2: Have the user(s) defined with an email address.
In version 6.5 of the SonicWall OS, this setting is in Manage > System Setup > Users > Local Users & Groups.
Here is one defined user:
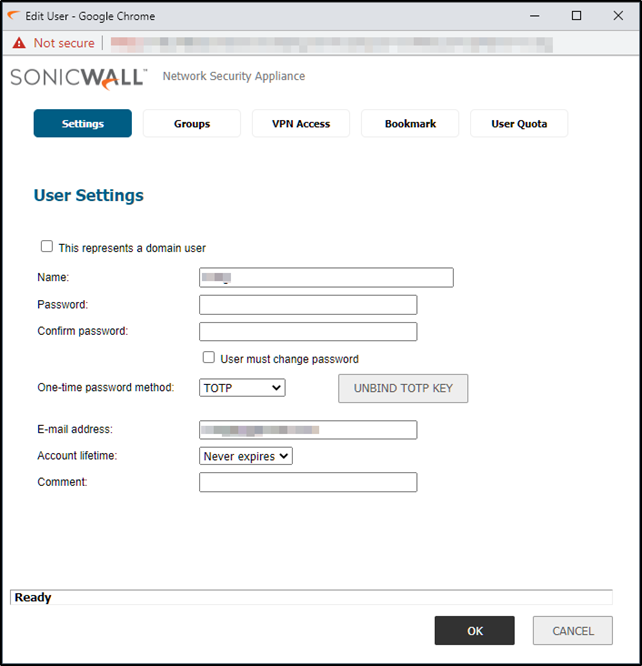
Step 3: Enable One-time password method.
For local users this is in the same section as defined above for creating the user.
The options here are:
- Disabled
- OTP via Mail
- TOTP
Note: the previous requirement in step 1 of configuring mail server settings is only used if the option of OTP via Mail is configured. OTP stands for One Time Password.
If OTP via Mail is selected, now when this user signs into VPN, they will receive a prompt for the secondary password, which has been emailed to them. It looks similar to this:

If TOTP is selected, have the user sign into the website for the SSL VPN connection and sign in. When signing in, it will prompt to configure MFA for an application. I used the Microsoft Authenticator just fine.
Here are the steps to connecting via the SonicWall MobileConnect app on an Android phone:
- Sign in.
- Enter the code received from your bind app.
- Connect to the VPN.
Setting MFA for Local Users
Keep in consideration that you likely don’t have local users configured in your SonicWall for SSL VPN connection, but rather have an LDAP connection to a domain controller for user authentication on the firewall. In order to have this set for users based in Active Directory, you would have to choose LDAP as the connection method for adding users in the SonicWall, make sure that email addresses are defined for the user objects in Active Directory, and then apply this One-time password method to a group of users. Please note that if you already have another MFA deployment, such as Azure MFA, that you should use that for consistency and ease of use for your users.
This solution works because it uses out of the box settings available now on your devices, granted that you have a SonicWall firewall appliance, a domain controller to sync users, or have local users. However, you should be aware that this would show up as a second entry on the Microsoft Authenticator app, and it will not use the same changing MFA code used for Microsoft 365 connections.
Have any questions about setting up MFA for your SonicWall firewall? Please contact us at any time!
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




