This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Why Do I Need Multifactor Authentication in Office 365? Isn’t a Password Enough?

Just 8-10 years ago, if you had a business, you needed email. And if you needed email, you needed a Microsoft Exchange server. It was just the way the world was. When you had your own email server, that meant you likely had an appliance or hosted service doing email filtering on your behalf. With that in front of your Exchange server, if someone wanted to attempt to login to your environment as one of your users, they would have to do a bit of digging and maybe even some social engineering just to get started. The Exchange server would likely have its own public IP address that is exposed to the internet over an encrypted port to allow users access to webmail or ActiveSync email on their cell phones, but because email was directed at the web filter or the service by the domains public MX record, it wouldn’t be obvious exactly where to try to login as the user to either brute force or otherwise compromise their password.
The public cloud was still something not being adopted with open arms; it was not mainstream. Times have changed. With the widespread of adoption of Office 365, now everyone that is using Office 365 has the same entry points:
- Portal.office.com
- Outlook.office.com
- Or simply office.com
It’s a great thing because it is so easy to remember. It’s also a great thing for the attackers, as they no longer need to search for the entry point to begin their attack. They can do a simple DNS record MX lookup on a domain, and if the record points to something.mail.protection.outlook.com, they know where they need to start their attack.
What Is Multifactor Authentication?
Multifactor Authentication is simply the use of more than one method to provide authentication to log into something. Most commonly implemented in 2FA or two-factor authentication, it is your two forms of ID in the digital world. Most commonly it is a password and something else. Samples of that something else can be a:
- Passcode visible in an app or device
- Phone call to a predefined number
- Application installed on a mobile device that prompts for confirmation
- Fingerprint
- Retinal scan
- Use of facial recognition
- Smart card
Now even though an attacker may have compromised your password that consists of the name of your dog and the year of your graduation, they still cannot access your data without the second authentication method.
How Do I Implement it?
Microsoft has made available a deployment guide here: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-getstarted
Users can define their own additional security verification factors by signing into this page: https://aka.ms/MFASetup
Quickly summed up, you:
- Log in to portal.office.com as a user that has the privilege to make changes to user accounts.
- Navigate to your users and find a user that you wish to implement MFA.
- Click on Manage multi-factor authentication.
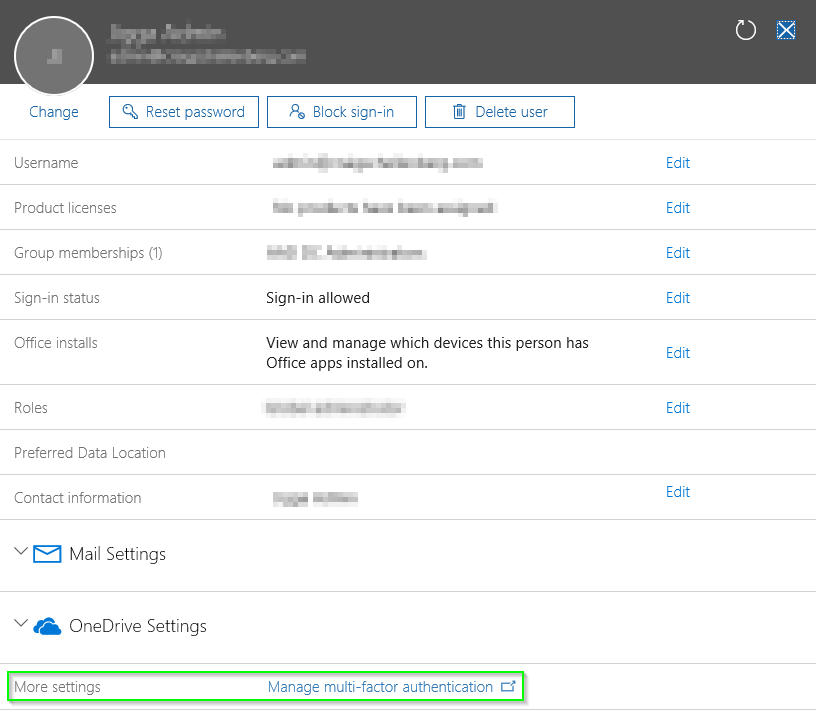
Alternatively, you could navigate straight to here: https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx
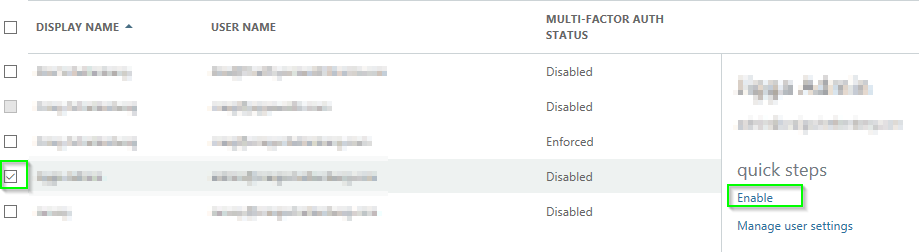
- Find the user you want to enable MFA for and click Enable.
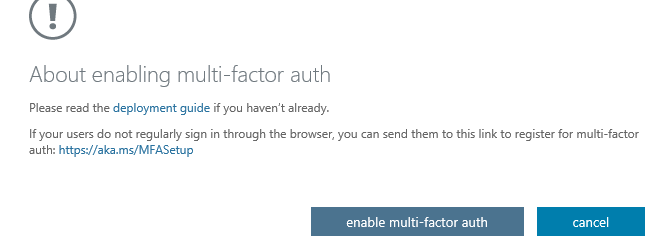
- You will get the “are you sure” secondary prompt that has a bit more information in it for deployment. Click enable multi-factor auth to continue.
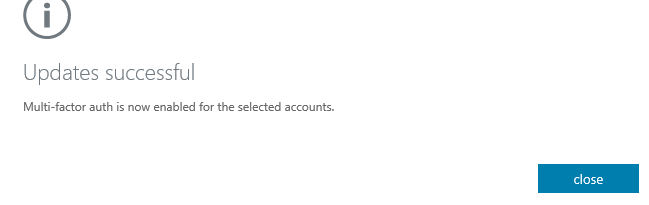
- And it is turned on!
So, what did it just do? What will the user experience be?
On the user’s next login to Office 365 they will be faced with a different prompt after successfully logging in as normal.
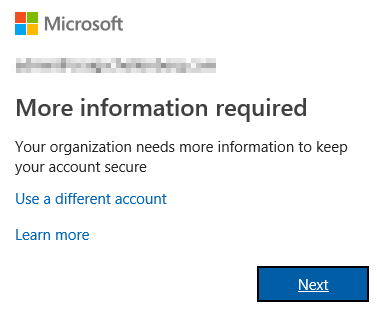
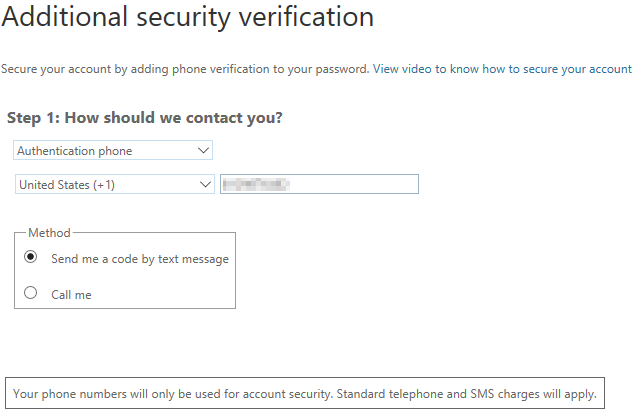
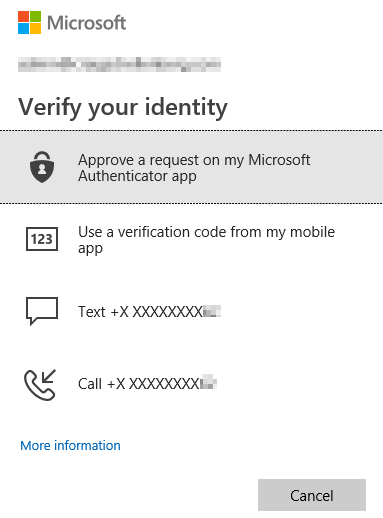
After clicking Next to continue, they will be prompted to choose which secondary form of authentication they want to use at this time. Their options are:
- Authentication phone (user defined cell phone)
- By phone call
- Or by text
- Office phone (administrator defined phone number on their account)
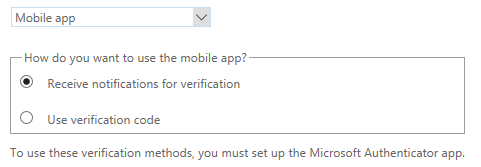
- Mobile app (Microsoft’s Authenticator app available on Google Play here or on iOS devices here.
I recommend either authentication phone with a text message or by use of the mobile app.
The authenticator app can have many different accounts set up simultaneously. I have no fear of even posting my current codes as they have already changed 24 seconds after I had taken the screen shot from my phone.
Then Microsoft will attempt to make sure that form of authentication works.
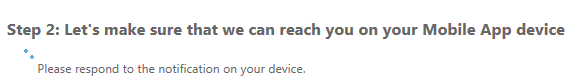
This prompt appeared on my phone for which I clicked APPROVE.
Microsoft will request a third form of authentication just in case the second factor isn’t available or working at the time.
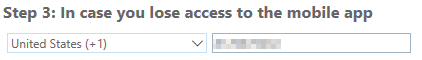
At the risk of being less secure, Microsoft introduces app passwords. These are meant to be used when Multifactor Authentication isn’t supported by the device as it isn’t using Microsoft’s modern login experience. Learn more here: https://docs.microsoft.com/en-us/azure/active-directory/user-help/multi-factor-authentication-end-user-app-passwords.
Modern phone apps and modern Office Applications do indeed support multifactor authentication and I highly suggest using it instead of the app password method.
Once completed with the process for creating the other forms of authentication, the next time the user logs in, after putting in their password they will see this screen if they chose the Authenticator App, or a similar screen if they chose another method.
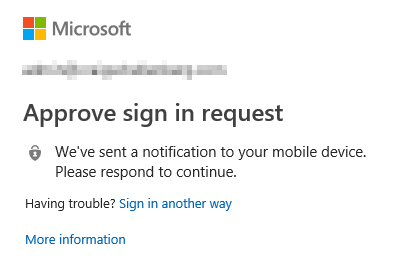
If the user doesn’t respond in a timely manner, the login will time out and the user will be given more methods for accessing their account which they have already predefined.
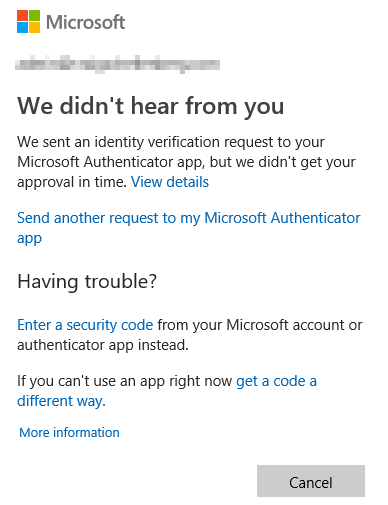
Options are available to bulk enable MFA on more than one account. Also, there is somewhat of tracking available for users that have configured MFA or haven’t. Again, visit this page if users will have one of the following three statuses:
- Disabled – MFA isn’t enabled for them
- Enabled – MFA is enabled for them but they haven’t completed giving Microsoft their other forms of authentication yet
- Enforce – MFA is enabled and is actively enforced in order to access the mailbox (this is what you want)
Now your users are more secure than they previously have been, and honestly, it wasn’t too hard to implement. Always remember to implement security in multiple layers of defense and rest easy that this layer is now protecting your users from the impostors.
Have any questions about setting up Office 365 Multifactor Authentication? Feel free to contact our tech team at any time!
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




