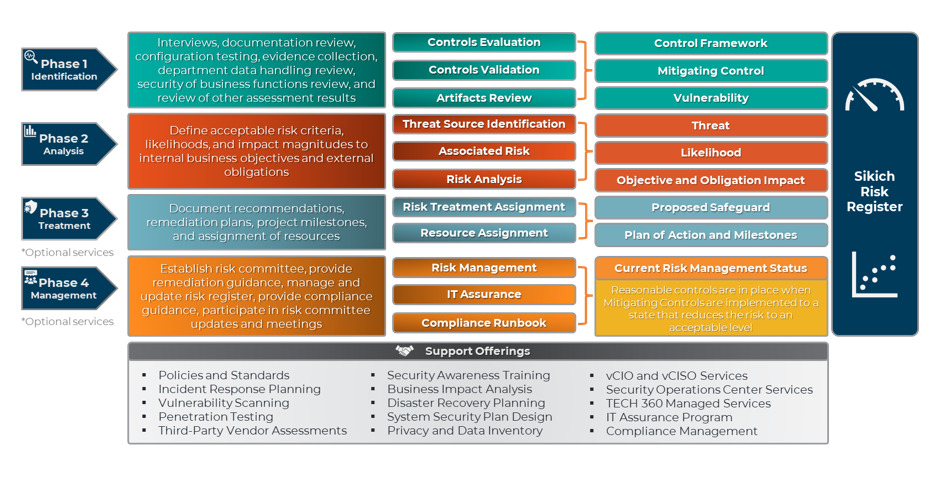
Our approach to risk
Our four-phase approach begins with controls evaluation and validation, where we evaluate the assessment scope against a subset of security requirements to identify vulnerabilities and document implemented controls that mitigate potential risks. Next, we move to risk analysis, where we evaluate vulnerabilities in terms of the risks they pose to information and systems and develop acceptable risk criteria to prioritize reasonable safeguards. In the third phase, we focus on risk treatment, providing recommendations for remediating risk to an acceptable level and providing a roadmap to establish an effective information security program. Finally, we assist with ongoing risk management, including identifying new risks to the organization and providing guidance for maintaining an effective risk management program.
The main phases of a risk assessment
1: Risk Identification
2: Risk Analysis
3: Risk Treatment
4: Risk Management
Why choose Sikich GRC?
Our risk management services are tailored to meet your organization’s unique needs. Our team of experienced risk managers has a deep understanding of the regulatory and compliance landscape and provides valuable insights into industry best practices. Our risk management services help organizations:
- Protect sensitive data
- Meet regulatory requirements
- Improve operational efficiency
- Strengthen the overall security posture of the organization
- Increase stakeholder confidence