This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Remote Access Software Best Practices

Remote access software is deployed by countless organizations across a variety of industries. As a practical method to manage environments without being physically present, it supports an organization’s ability to maintain multiple satellite locations or offer an option for traveling staff to get access to a system and address an error.
This practicality comes with risks. Unauthorized attackers can utilize the same remote access software to access an organization’s environment if the remote access software is not protected properly. As part of the forensic and incident response engagement Sikich performs, Sikich regularly discovers that attackers exploited remote access software to gain access to the environment.
Fortunately, in many cases, an organization can take steps to minimize risk such that remote access can be used safely and securely. While the software used in these examples is LogMeIn (one of the more popular cloud-based software options available), these principles should be applied to any product that an organization implements. If the product that you or your team currently uses does not support these recommendations, then it may be best to switch to a different product.
Enabling Multi-Factor Authentication
Enabling multi-factor authentication is one of the most important steps a user can take in securing a user account. This feature can prevent an attacker from utilizing an account if a password is compromised. First, let’s understand what multi-factor authentication means:
“Multi-factor authentication (MFA) is a method of confirming a user’s claimed identity in which a user is granted access only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something they and only they know), possession (something they and only they have), and inherence (something they and only they are).”[1]
Some users utilize a one-time password sent to an email account, believing that they have enabled multi-factor authentication when, in fact, they have not. This action is considered multi-step rather than multi-factor authentication because it is utilizing only one factor: something they know (i.e., passwords are often used to log in to both remote access software and an email account on the same computer).
For most people, the optimal method to employ multi-factor authentication is to utilize their smartphone device (something they have). LogMeIn, via a method somewhat confusingly referred to as “Two-step verification,” allows users to receive a push notification (an automated message sent by the application) through LogMeIn’s application, LastPass Authenticator. Responding to the notification serves as a second authentication factor (in addition to the password being entered). Receiving a token via SMS (text messaging) is also an option but is considered deprecated by the National Institute of Standards and Technology (NIST).
Sikich strongly suggests utilizing push notifications via an application since it is often more difficult for attackers to intercept or manipulate. If push notifications or text messaging are not options, oftentimes a time-based one-time password option, such as that popularized by Google Authenticator, is available. Note that, when using time-based one-time password options, the private keys used to generate the one-time passwords need to be protected on the device. One way to do this is to enable device or full-disk encryption.
To turn on multi-factor authentication in LogMeIn, access the LogMeIn portal and access the “Settings” option on the top right of the menu, then select “Account Settings.”
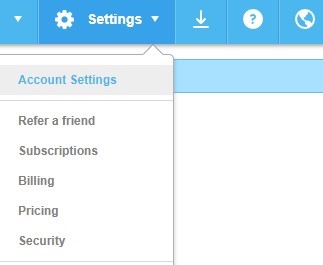
You will find the option to turn on “Two-step verification” in the security “Section.”
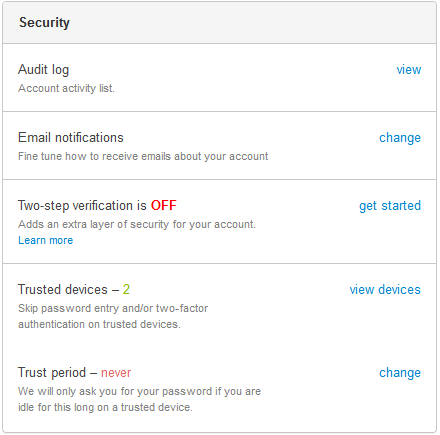
Here you can decide whether to use the LastPass Authenticator application or receive a text message. LogMeIn also requires you to set up a backup authentication method. You can choose to enable LastPass Authenticator or a one time passcode via email for this purpose. Be advised that utilizing an email account is considered the less secure method as most users utilize a password (something they know) to access email.
Please note that information security best practices state that passwords should not shared by different accounts. For this remote access tool, the password for your email and LogMeIn account should not be the same.
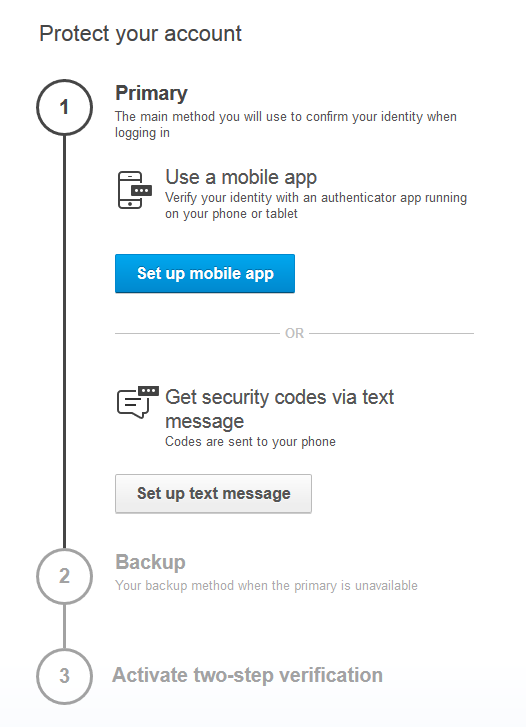
With multi-factor authentication enabled, you can greatly limit the risk from compromised remote access account credentials. Please be sure to consider any laws or standards that entities may be required to follow when applying multi-factor authentication to remote access software.
Extending Logs
Most remote access software can be configured to maintain records or “logs” of activity on remote access accounts. Sikich’s experience, however, has been that organizations rarely have remote access logs available from during a window of intrusion. Remote access logs can be crucial for incident responders to gain a fuller understanding of how an intrusion occurred and what data was affected. An M-Trends Report for 2019 found that it took on average of 78 days for companies to detect an intrusion.[2]
While the default setting on many remote access software applications may be to retain logs for 90 days, it is important to centralize the logs and retain them for at least a year. If remote access logs are not available for the timeframe of an intrusion, incident responders may not be able to build a complete story or timeline, and questions like, “What data did the attacker access?” may never be answered adequately.
To expand the amount of logging retained in LogMeIn, one can visit the options tab in the LogMeIn control panel within the local LogMeIn client on the host computer. From there, select the “Preferences” option and then the “Advanced” tab. In the “Event Logs” section, the number of days of retention can be changed.
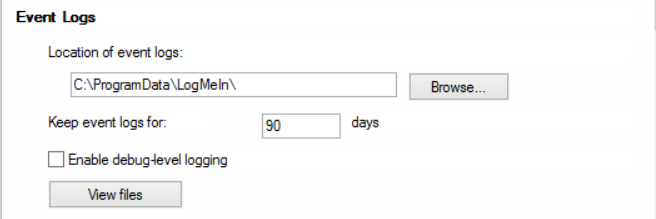
Sikich recommends that logs be retained for at least one year. Again, if applicable, consider any laws or standards that may apply to your environment in terms or retention requirements. If centralized logging is used within your environment, route these logs to be included as well. The amount of logs generated by LogMeIn are small enough that the retention period can be increased beyond 90 days without impacting resources.
Conclusion
Remote access software is useful as it allows access to systems from almost anywhere. However, utilizing it insecurely increases the risk to your environment. Attackers often use remote access software as a method of infiltrating environments. Additional steps should be taken to further secure remote access. Multi-factor authentication should be implemented to prevent an attacker from utilizing credentials in case they are ever compromised. Expanding event log retention beyond 90 days increases the visibility of attacker activity if accounts are ever compromised.
While there are additional steps that can be taken to further harden remote access, taking the aforementioned actions can immediately help safeguard your remote access and preserve critical information for incident responders in case an incident does occur.
Have any questions about remote access security? Contact our experts at Sikich at any time.
[1] Multi-factor authentication (https://en.wikipedia.org/wiki/Multi-factor_authentication)
[2] https://www.fireeye.com/current-threats/annual-threat-report/mtrends.html
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




