This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Mobile Device Mailbox Policies in Exchange Online

In today’s fast-paced business environment, the need for efficient communication and collaboration is paramount. With the widespread use of mobile devices, it’s crucial for organizations to ensure that their email systems are secure, compliant, and accessible from anywhere. Microsoft Exchange Online, a part of Microsoft 365, offers a comprehensive solution for managing mobile device mailbox policies. In this blog, we will delve into the world of mobile device mailbox policies in Exchange Online, exploring their importance, configuration, and best practices.
Reference: Mobile device mailbox policies in Exchange Online | Microsoft Learn
Mobile Device Mailbox Policies are a set of security and access settings that are applied to mobile devices when they connect to an Exchange Online mailbox. These policies are designed to ensure the security of your organization’s data while allowing users to access their email, calendar, and contacts from their mobile devices seamlessly.
Ensuring the security of your organization’s data is paramount. Mobile devices are a common target for cyberattacks, and a breach can have devastating consequences. Mobile device mailbox policies help in securing sensitive data by enforcing security measures such as PIN requirements and encryption.
These policies can also enhance user productivity. By providing seamless access to email, calendars, and contacts on mobile devices, employees can stay connected and efficient even when they’re on the move.
How to Configure Mobile Device Mailbox Policies
- Configuring mobile device mailbox policies in Exchange Online involves several steps:
- Access the Exchange admin center in Microsoft 365.
- Go to the “Mobile” section then “Mobile device mailbox policy” and create a new policy or edit an existing one.
- Configure device access rules, security settings, and mailbox access settings as per your organization’s requirements.
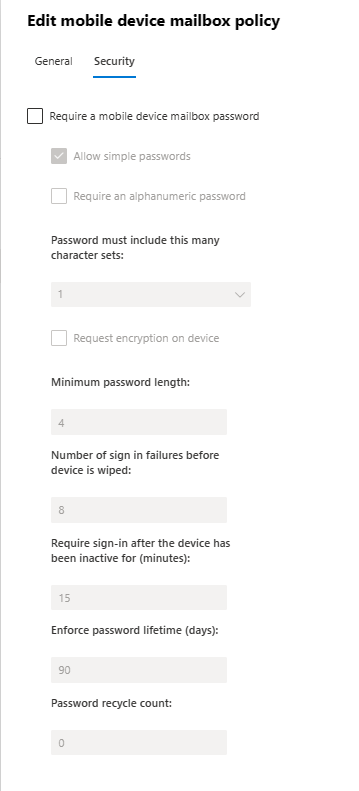
- From the Exchange admin center, we can use the GUI to configure options to require a mobile device mailbox password, password requirements, and number of sign in failures before the device is wiped.
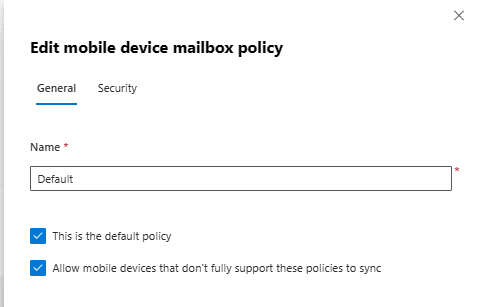
We can select to make the policy the default policy, which will automatically assign the policy to all users.
We can modify additional settings that aren’t available via the Exchange admin center, and we can assign specific policies to specific users by utilizing the ExchangePowerShell. I recommend doing this to pilot the policies with a small group of users before applying a policy company wide.
Reference: Set-MobileDeviceMailboxPolicy (ExchangePowerShell) | Microsoft Learn
Best Practices for Mobile Device Mailbox Policies
To make the most of mobile device mailbox policies in Exchange Online, consider these best practices.
Tailor Policies to User Roles:
Different roles within your organization may require different levels of access and security. Create policies that align with specific job functions and responsibilities.
Regularly Review and Update Policies:
Technology and security threats evolve over time. Periodically review and update your policies to ensure they remain effective and compliant.
Educate Users:
Provide training and guidelines to users on how to secure their mobile devices and follow best practices for mobile access.
Use Conditional Access Policies:
Combine mobile device mailbox policies with Azure AD Conditional Access policies for additional security and control. Blocking legacy protocols and forcing the use of the Outlook app is best practice.
Conclusion
Mobile device mailbox policies in Exchange Online are an essential component of modern business operations. They provide the means to secure sensitive data, maintain compliance, and enable remote access for a mobile workforce. By following best practices and configuring policies that align with your organization’s needs, you can harness the power of Exchange Online to ensure secure and efficient mobile device access. So, take the necessary steps to implement and manage these policies effectively and stay ahead in the era of mobile productivity.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




