This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Restricting Access to Microsoft Azure PaaS Databases from Microsoft Azure Virtual Machines

The Problem
PaaS (Platform as a Service) SQL instances in Azure take a lot of work out of having to maintain and license an instance of SQL on on-premise or collocated hardware. When using any service on premise or in the cloud due diligence to secure access to it should never be overlooked. When setting up a SQL server in Azure, there is a default setting that should be changed to properly secure your instance. If you currently administer a PaaS instance of SQL running in Azure, go look to see what your setting is set for right now and read the rest of this blog post to find what you need to do to secure it. To find it, open https://portal.azure.com and sign in to your subscription. Browse to SQL servers, pick your SQL server, and under Settings, choose Firewall / Virtual Networks.
Once there, have a look at the very top option. It is titled “Allow Access to Azure Services.” At the time of this blog, there is no other information describing what this button does in this section other than the five words on top of the button. The default selection for this is “ON.”
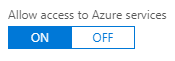
At first glance it would appear you would want this to be left on, especially if you have Azure Virtual Servers that need access to the Azure PaaS instance. However, you do not want this left on! This default setup of a new Azure PaaS SQL server will leave network access to your PaaS database open to all virtual servers running on Azure’s cloud platform, from any subscription (not just your own). Other Azure clients will have access to the SQL database(s) if:
- the server name (something.database.windows.net) is known, and
- the SQL login credentials are known.
Both things could be brute forced, however.
The Answer
Secure the PaaS instance by either turning off access to Azure services alone or in combination of using a SQL Service Endpoint and adding the virtual network to an allowed list.
Option 1
If you do not have any Virtual Servers in Azure that need access to the PaaS instance there is a simple fix. Navigate to https://portal.azure.com and sign in to your subscription. Browse to SQL servers, pick your SQL server, and under Settings, choose Firewall / Virtual Networks. Click OFF under Allow Access to Azure Services and click the Save button.
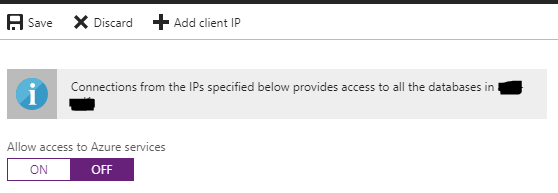
That’s it! You have taken away network access to the vast amount of virtual machines that exist on Microsoft Azure’s cloud.
Option 2
If you do have servers in Azure that need access to the PaaS instance there are a few more steps. Navigate to https://portal.azure.com and sign in to your subscription. Browse to Virtual Networks and choose the virtual network that the virtual servers exist on that will need access to the SQL PaaS instance. Then under Settings, choose Service endpoints.
Note: Just this month, February 2018, Virtual Network Service Endpoints came out of “preview” and are now fully supported by Microsoft. To learn more about Virtual Network Service Endpoints, visit: https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-service-endpoints-overview
Click the Add button.
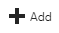
Choose the Microsoft.Sql service and the subnet within the virtual network that the Azure virtual servers are on, and click the blue Add button to continue.
We are almost halfway there. Once the endpoint is associated to the virtual network, navigate back to your SQL PaaS server (browse to SQL servers, pick your SQL server, and under Settings, choose Firewall / Virtual Networks.)
Explanation:
(If you don’t care to understand the different sections on this page skip down to the “Action” section below.)
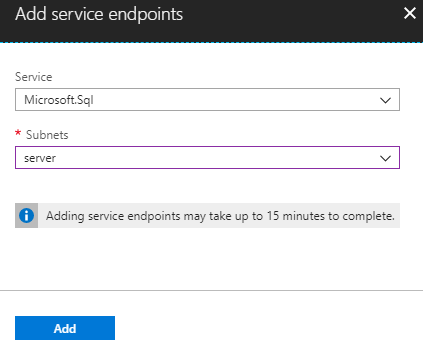
This section can be confusing as you may be tempted to think if you add a rule with the public or private IP of your Azure virtual server that would allow the required access. This section however is only for servers and environments not hosted on Azure’s cloud. This section would be used to secure access to the PaaS instance from an on-premise or collocated application server needing access to the database(s).
In the below example, if 12.34.56.78 was the public IP of an Azure VM, the rule “allow Azure VM” would do absolutely nothing. If the “Allow access to Azure services” button is turned off, there would be no access to the Azure PaaS SQL instance. If 98.76.54.32 was the public IP of your on Premise non-Azure server needing access, this is the correct location to add access to it and the rule “allow on-premise VM” would allow the required access.
Action:
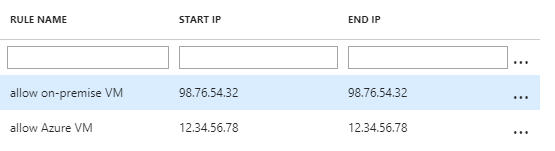
In the bottom section, there is a section labeled “Virtual Networks.” From here click + Add existing virtual network.

From here give a rule name, select the Azure Subscription the virtual network lives on, the virtual network itself along with the subnet. Click OK.
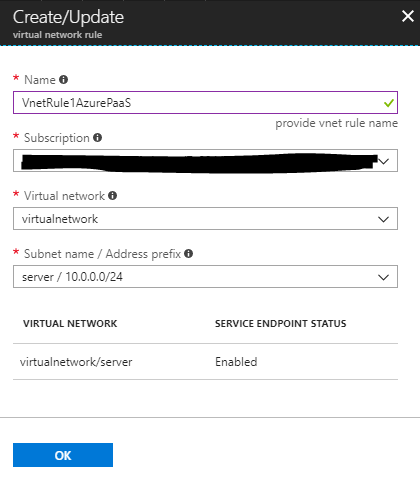
Note: The column for “Service Endpoint Status” should state “Enabled.” If it does not, you have either skipped the first step to add the Service Endpoint to the virtual network, configured it incorrectly, or haven’t given it time to create.
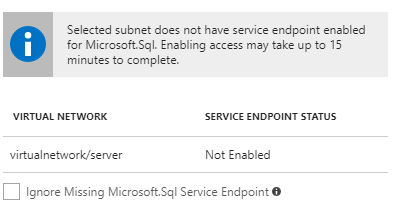
If you mouse over the informational “i” it reads: “Virtual machines in the subnet will not be able to connect to the SQL server until Microsoft.Sql service endpoint is added to the subnet.” If this is the case, make sure you configure the service endpoint correctly.
Once set up correctly, the rule will show similarly to this:

And finally, turn off access to all Azure virtual machines by clicking the OFF button on “Allow access to Azure services” and click Save.
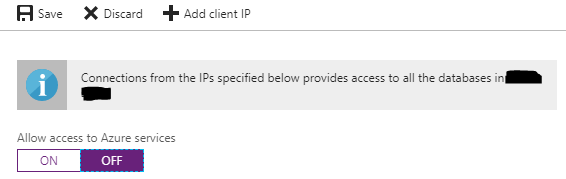
Congratulations! You have now secured your PaaS database to just your own Azure virtual network.
Want to learn more about Azure? Get more information here.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




