This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Detecting and Recovering From a Compromised Account

Sadly, I am often times called into assist with remediation efforts following an account within Office 365 getting compromised. I will be the first to say that this is definitely not the result of Microsoft falling short on their security measures, rather, this is the result of passwords being phished/guessed/stolen. I have seen a handful of those original phish messages and some of those are outright incredible. They are so well put together that I can easily see how they got through people’s defenses. The worst ones are the internal ones, mostly because they exploit a relationship where our guard is already down because we know the person. Overall, they are clever, they are well written, and they contain all the right language/lingo.
How to Detect Compromised Account
A rather easy tip I would offer on how to detect if your account has been compromised is to: check your Outlook rules! I know, a rather odd one, however, this is probably the biggest tell I have seen to determine if an account has been compromised. In almost every case I have been involved in, I find something in here that shouldn’t be. Here is why: in an attack scenario, after credentials have been phished/guessed/stolen/etc., the attacker’s first objective is to harvest information. Once enough information is obtained, they create a crafty phishing message to send out (internal/external). To cover their tracks and avoid getting the phish stopped prematurely (before pay day!), they set up rules to automatically remove email responses.
Where to look?
In Outlook, in the Home tab, under the Move section, click on Rules, then click on Manage Rules & Alerts.
Looks like I only have 1 rule right? Wrong!
Check out the message at the bottom (in the green highlight).
Without the green highlight, you likely would have glossed over that warning.
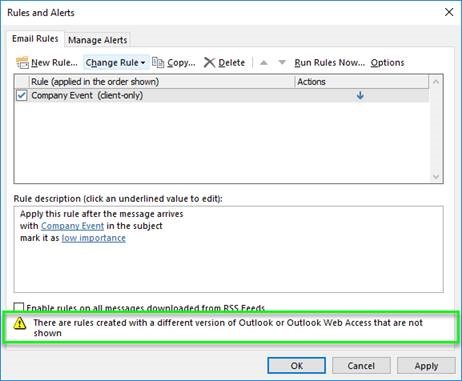
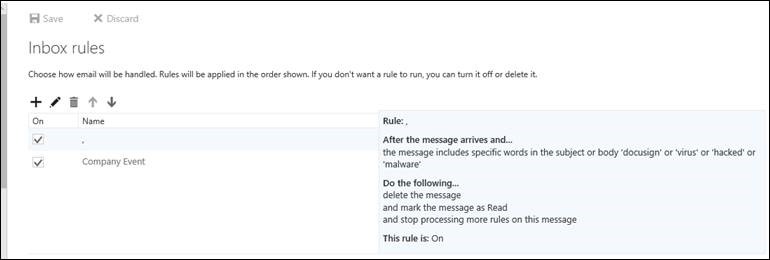
Only after logging into my webmail page and looking at my rules there would I see the details!
Clearly, some major red flags with what we see:
- I see more rules than I do in Outlook,
- the name of the rule is abnormal,
- the criteria of the rule to filter on abnormal keywords, and
- that the emails are just being deleted (I have also seen cases where the action is to move the messages into the RSS Feeds folder or Notes folder).
Overall, this is just not a normal rule to create.
How to Recover Compromised Account
Rather straight forward procedure on the immediate items:
- Screenshot and then delete the Outlook rule. You will want to provide IT with the details of the rule.
- Change your password.
- Get IT involved.
- Notify recipients.
It will be the third step that is the bulk of the work. Most of the effort is forensic in nature, things such as when was the account compromised, where did the attack originate, and what items were touched (insurance companies would need this type of information). IT would also be able to assist with determining who received those phishing messages from your account so that you can notify the people who received your phishing message.
In addition to these, I always look at other available inexpensive services (i.e. MFA) or inexpensive add-ons (i.e. ATP) to enhance the security posture and make any further breaches less likely. If those services have already been deployed (ATP for example), that service is reviewed for any additional configuration changes that could be made.
How to Safeguard Against Phishing
Not that these items are fail proof, but my hope is that they do make it hard enough for an attacker that I am not worth enough effort for them to target my account(s).
Passwords
We have all heard at one time or another, use strong passwords, change passwords often, don’t use the same password for different services, etc. While that advice is sound and absolutely true, that message is so routine that I think most people at this point just ignore it. I suggest using a password management tool to help you meet strong password requirements. Nobody likes to remember passwords, especially if they have a huge list of them for all sorts of services/accounts. There are many great tools available to maintain and keep our passwords safe – some free, others paid. Some of the better known ones like Dashlane, Keeper, and LastPass are all great options. With tools like that, you can make strong passwords like “ePPGq#VCu8aY&w4,” without having to remember them or type them out!
Use Multi-Factor Authentication
This is also sometimes called 2-step authentication. While I would be the first to admin that it adds a little bit of a burden as there is an extra step, I always keep telling myself that the little bit of an extra effort that I have to go through is a whole lot less effort that I would have to do to deal with all the work if I ever saw the rule mentioned above in my own mailbox.
Not that this is an endorsement of any kind, but personally I use LastPass with MFA enabled for safekeeping my own passwords. Need to talk to someone about strategic security planning for your organization? Sikich is here to help. Let’s chat.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




