This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Vulnerability Allows Malicious Domain Registration

I recently was reading a publication on security and came across this major zero-day vulnerability that has affected many different SaaS (Software-as-a-service) platforms and some major domain registrars.
This vulnerability is particularly interesting as it allows domain registration to include specific “homoglyphs.” You may be asking, “What is a homoglyph?” A homoglyph is a letter, character, or glyph with shapes that appear identical or very similar to another letter, character, or glyph.
Think about the most common ones, the letter “O” (as a capital) and the number “0” (zero). They look very similar but are, in fact, very different. Another one would be the letter “l” (lowercase) and the letter “i” (capital). This can be deceiving as some sites may look like the legitimate website when navigating to them from a hyperlink in an email.
The nature of this attack can be very similar to an IDN homograph attack, which according to Wikipedia, is a way a malicious party may deceive computer users about what remote system they are communicating with, by exploiting the fact that many different characters look alike (i.e., they are homographs, hence the term for the attack, although technically homoglyph is the more accurate term for different characters that look alike).
This attack usually is attempting to steal credentials or drop malware on to unsuspecting users. This is particularly dangerous when the domain is of high value. See some examples below of these malicious domains.
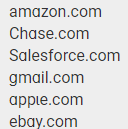
Look at the first one in the list—amazon.com—you can see the letter “a” is different for each occurrence of the letter. The first a is the correct one, but the second “a” is the homoglyph and where the spoofing starts. Note particularly how unless you are actively looking for this, you most likely will not notice the differences.
I have seen emails like this out in the wild as recently as a few weeks ago, which means this is active and in use today. Also, you should keep in mind that these can be utilized in any form of digital communication where we are expecting users to click on links. This includes many business functions like email, chat, collaboration applications, documents, and PDF files. This is an example of a highly targeted social-engineering or phishing attacks against users, customers, or employees of the spoofed domain.
If you want to learn more about how Sikich can protect you from malicious domain registration and other new emerging threats, reach out to our team now and start the conversation!
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




