This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Phishing, It Can Happen to You: Identifying Phishing and Scam Emails
Phishing and scam emails are sent on a daily basis to millions of people. Not everyone can catch them every time. In fact, anyone, including one of the most popular technology teams on YouTube, Linus Tech Tips (LTT), can fall victim to phishing. This post is meant to help you to identify these sorts of scam emails so you can avoid falling victim to them.
Understanding What Phishing and Scam Emails Are
Phishing and other scam emails are generally mass produced and sent to as many email addresses as the threat actor can find or pull from public resources. However, attacks involving these types of emails can be more targeted, as was the case in the LTT takeover, which involved an employee opening what they thought was a PDF file from one of their sponsors that turned out to be a malicious Windows screensaver (.scr extension) file.
The threat actor named the file in such a way that they gave it a double extension (e.g., filename.pdf.scr), since Windows defaults to not showing file extensions. This led the victim to believe that the document they were opening was a PDF and not an executable. The screensaver file contained malware that then stole information—such as session information and saved credentials—from their browsers and allowed the threat actor to take over not only the LTT YouTube channel, but several other related channels as well.
Hackers and scammers target all sorts of people for various reasons in the hopes of stealing personal data, money, or other valuables. However, their emails normally offer a few key giveaways that can help you identify them as phishing or scam emails, including:
- Grammar and spelling errors
- Altered domain names used for email address and links
- A sense of urgency
- Unusual requests
- Unfamiliar greetings
What To Look For
For the purposes of demonstration, I wanted to give an example of what several scammers have recently sent me in connection with an item that was up for sale on Facebook in the United Kingdom (UK).
Banking is done differently in the UK. While routing and account numbers are considered sensitive in the United States, that isn’t the case in the UK, and people freely give them out in order to transact with others. What’s more, banks don’t hold money in escrow until a transaction is completed. If a threat actor were to actually send money for an item, they wouldn’t be able to get it back. The key to these scams, then, is to somehow trick the victim into thinking their payment is being held by a bank until it is confirmed that the item has been sent.
When the spam filter flags a scam email
One of the first emails I received from a scammer was flagged by my spam filter, and the scammer knew this was going to happen. The email, which supposedly came from the scammer’s bank, was marked as spam, which led to the scammer telling me separately, “Check your spam folder in your email, you should have confirmation that the funds were sent.”
Altered Domain Names
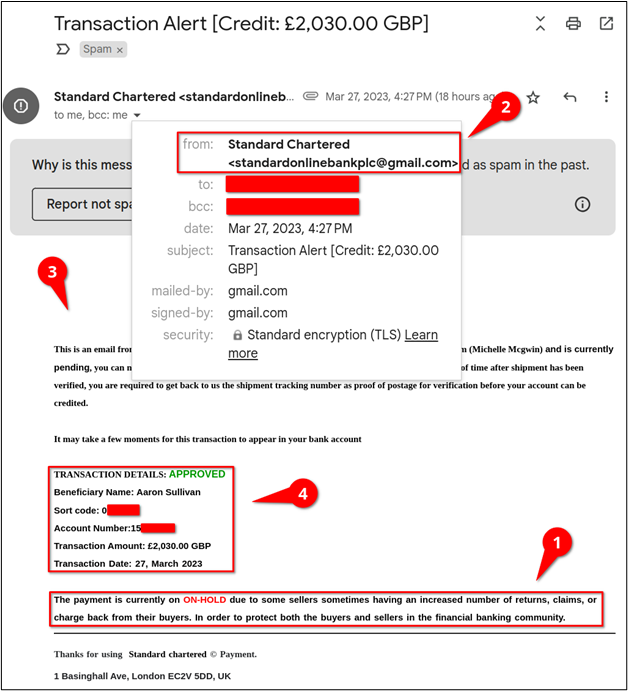
I checked my spam folder and found an email that was supposedly from Standard Chartered, a UK bank. From doing a quick check, you’d find that Standard Chartered owns the sc.com domain. Therefore, it would be fair to assume that emails from Standard Chartered would originate from sc.com.
The following screenshot shows the email I received, which contains several of the previously mentioned scam giveaways. First, as previously stated, the domain for Standard Chartered is sc.com. It’s possible that the bank could own several other domains, but why did this email come from a gmail.com account (see item 2)? While everyone knows some small businesses that use gmail.com email addresses, the likelihood of a large bank doing so is very slim.
Unfamiliar Greeting
While the email supposedly came from a bank, which knew my name, the message lacked a greeting (see item 3).
Grammatical Errors
The entire email is riddled with grammatical errors (e.g., “The payment is currently on ON-HOLD”), and the wording throughout is very confusing (see item 1). For what seems like it would be a templated email, you would expect most institutions to have proofread the content such that the messaging was clear for the recipient.
Lastly, if you notice, there is a space behind each colon except for the “Account Number” (see item 4).
Sense of Urgency
The sense of urgency related to this scam actually came from messages the scammer sent on the side through Facebook. The scammer tried to guilt trip me, saying that the money being held by the bank had already been debited from their account and I needed to send them the item immediately if I wanted my money. As previously mentioned, this was unusual, because the banking system in the UK doesn’t hold money in escrow until they can prove an item was shipped. The strain on the banking system would be astronomical; it’s unrealistic to expect a bank to validate shipping for every item sold and shipped on third-party sites.
When the scam email bypasses the spam filter
The second scam email we’ll look at was a little more sophisticated and bypassed the spam filter. However, there were still several giveaways with this email that tipped off that it was part of a scam.
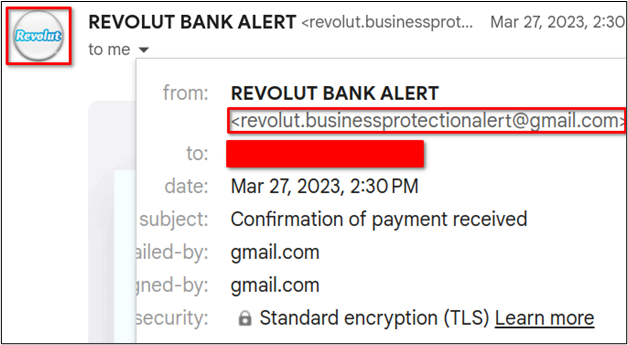
Altered Domain Names
First, the email claimed to be from Revolut, a banking services company, that owns the revolut.com domain name. However, the email once again came from a gmail.com address. In this case, though, the scammer changed the profile photo for the account to add a layer of sophistication.
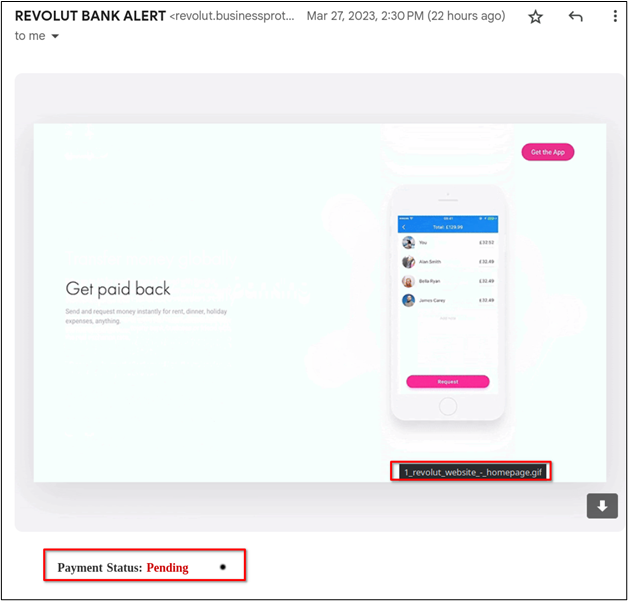
The start of the email included a GIF pulled from the Revolut bank web page to add animation into the email for a greeting. There was also an animation for payment status that made it look like payment was pending.
Unfamiliar Greeting
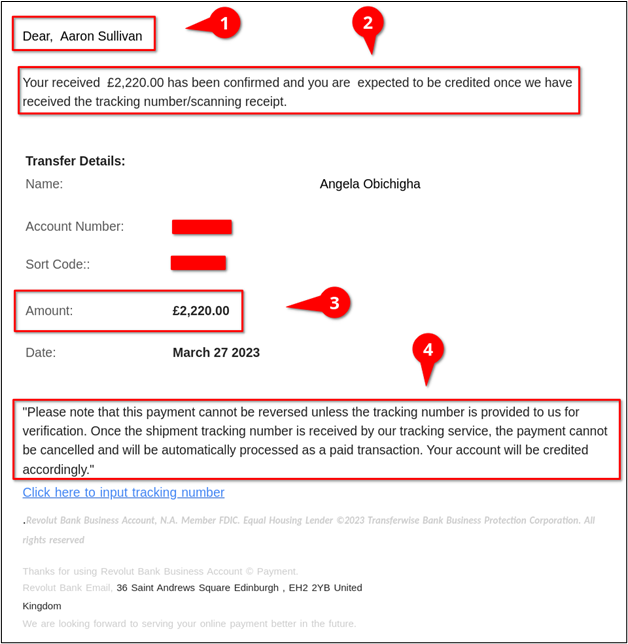
This message didn’t include the unfamiliar greeting tipoff. In the body of the email, shown below, the scammer actually added a custom greeting, which made the email seemed targeted and added to the sophistication level (see item 1).
Grammar Errors
This email again included several grammatical errors (see item 2).
Sense of Urgency
The messaging was also designed to create a sense of urgency. Telling someone that their bank has received payment creates an expectation that the person will see the money show up in their account shortly.
Additional Layers of Sophistication
This email added a new layer to the scam. The email shows that there was a £200.00 overpayment (see item 3). Scammers do this in the hopes that, once the package has been shipped, they can request the overpayment back and blame a typo, expecting that most honest people would be happy to return the supposed overpayment. In this case, though, the victim won’t be receiving any money, and would actually be sending the scammer £200.00 of their own money in addition to the item.
There was also some additional unusual language included in the request (see item 4). The email claimed that the transaction could not be reversed unless the victim provided tracking details. Why would the victim want to reverse the payment if they had already sent the item for which they were being paid?
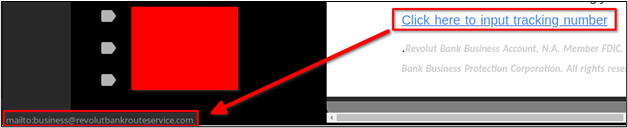
 A final clue that this email was related to a scam was a link provided for the victim to input the tracking number once the item shipped. As shown in the following image, the link was actually set up to send an email to business@revolutbankrouteservice[.]com.
A final clue that this email was related to a scam was a link provided for the victim to input the tracking number once the item shipped. As shown in the following image, the link was actually set up to send an email to business@revolutbankrouteservice[.]com.
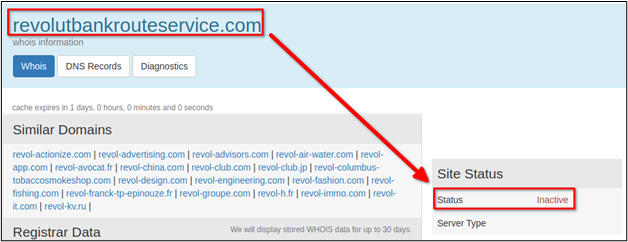
A quick search showed that the domain wasn’t owned by anyone and was inactive. It’s possible that this could have been a typo and the scammer messed up setting up the link, or the scammer just hoped that, by the time the victim checked the link, the item would have already been on its way and their scam would have been successful.
How to Protect Yourself
In looking at a couple of real phishing/scam emails that were sent to me, we saw one unsophisticated attack and one more sophisticated attack. Regardless of the sophistication level, these sorts of scams must be resulting in some level of success, otherwise scammers wouldn’t be bothering with putting them together. Unfortunately, the odds are that at least some people will fall for these sorts of scams, and no amount of security can protect and identify all scams. Just look at Google’s spam filter—it caught one attack but not the other.
So what does this mean in terms of protecting your business? Scams like these target businesses on a daily basis, and it only takes one employee to click a malicious link or download a malicious file that could open the door for a threat actor to breach the organization. The threat actor could then exfiltrate data, steal funds, or use ransomware to encrypt systems.
Maintain Threat Awareness
A great way to protect yourself and your organization is to focus on raising and maintaining awareness of current cybersecurity threats and scams. Train yourself and your users on what to look out for, not only on corporate systems but also their home systems if they work remotely.
Have Penetration Tests Performed
To evaluate how prepared your organization is to face the latest attacks, have a cybersecurity firm perform penetration testing that includes social engineering. The social engineering will put your employees to the test to see how they’d respond when presented with potential attacks or scams without having to worry about the fallout that comes from real-world attacks. This can help minimize the likelihood of employees falling victim to such attacks in the future.
If you are interested in learning more about opportunities to improve your security posture through security awareness training or social engineering, reach out to Sikich’s team of ethical hackers. We will work with you to create a testing and training program that aligns with your specific cybersecurity goals.
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.




