Nowadays, you can use your smart phone to lock your front door from anywhere. And that door can have a doorbell that lets you see who’s at your home, even if you’re not. Perhaps you’re at the grocery store checking that you’ve got everything on the shopping list that your refrigerator sent you.
More and more, the devices we use daily are becoming “smart” and/or “connected” devices, meaning they can connect to other devices or networks to communicate. This interconnection of devices that historically had no ability to connect to the Internet, for example, home appliances, vehicles, and medical devices, has come to be referred to as the Internet of Things (IoT). It is estimated that, by 2020, there could be as many as 20 billion connected IoT devices.
As the number of devices with the ability to connect and communicate with one another over various networks increases, so too does the number of vulnerabilities being discovered that are associated with these devices. These vulnerabilities can potentially lead to network compromises, identity theft or device takeovers to name just a few possibilities.
From a security standpoint, a concern is that many IoT devices, at least at this point in time, run insecure and vulnerable embedded firmware. To understand the potential dangers related to exploitable IoT vulnerabilities, you can take a look at the post “5 Infamous IoT Hacks and Vulnerabilities” from IoT For All, which discusses:
- The cyberattack related to the Mirai DDoS botnet, in which a massive distributed denial-of-service (DDoS) attack using an IoT botnet took down large parts of the Internet across North America and Europe.
- Virtual carjacking, where researchers were able to exploit a firmware update vulnerability in which they were able to remotely control a vehicle over a cellular network.
- The lack of encryption or authentication for Wi-Fi baby heart monitors, which could let attackers take over the devices and keep alerts related to an infant’s cardiac conditions from being sent to parents.
- The Devil’s Ivy Rube-Goldberg attack that made it possible for hackers to control security cameras and access video feeds within buildings to capture potentially sensitive information.
- A data breach related to a children’s toy that exposed millions of voice recordings between parents and their children.
In an effort to help device developers and manufacturers better secure and harden IoT devices and networks, the Open Web Application Security Project (OWASP) Foundation recently released an updated version of their Top 10 IoT vulnerabilities.
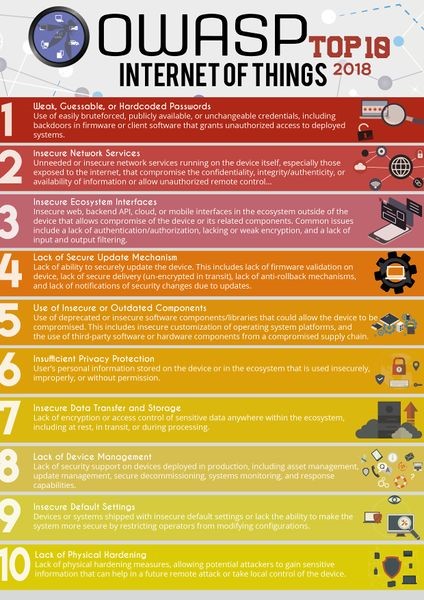
The OWASP Top 10 IoT vulnerabilities list primarily helps guide IoT hardware designers and software developers in the creation of secure solutions. While most people aren’t creating IoT devices, the list also suggests some steps organizations and individuals should take when selecting and deploying IoT solutions, including:
- Researching the reputation of the vendor and solution, including reviewing security notices
- Implementing a secure, isolated network environment for IoT systems separate from other networked systems
- Setting strong, unique passwords for IoT interfaces
- Selecting IoT solutions that provide a centralized management interface for managing passwords, configurations and firmware updates
- Enabling multi-factor authentication if available
- Hardening devices by changing default settings to the most secure option following vendor instructions
OWASP also provides additional security guidance for manufacturers, developers, and consumers.
The availability of IoT devices offers several benefits, including in terms of convenience and efficiency. And while it’s unlikely that the everyday consumer can either fully secure their IoT devices on their own or completely avoid IoT devices, being aware of the potential risks can put a consumer in a better position to leverage IoT devices in a more informed and secure manner.
Have questions about your organizations own IoT security? Don’t hesitate to reach out to us at any time!
This publication contains general information only and Sikich is not, by means of this publication, rendering accounting, business, financial, investment, legal, tax, or any other professional advice or services. This publication is not a substitute for such professional advice or services, nor should you use it as a basis for any decision, action or omission that may affect you or your business. Before making any decision, taking any action or omitting an action that may affect you or your business, you should consult a qualified professional advisor. In addition, this publication may contain certain content generated by an artificial intelligence (AI) language model. You acknowledge that Sikich shall not be responsible for any loss sustained by you or any person who relies on this publication.









