The Cybersecurity Maturity Model Certification, or CMMC, is a framework designed to ensure the protection of sensitive unclassified information shared by government agencies with its contractors and subcontractors. As part of this model, the Federal Information Processing Standard, or FIPS, needs to be applied to devices that have access to sensitive unclassified information. FIPS is a set of standards for data security and computer systems, primarily focusing on cryptographic modules and ensuring secure data processing. FIPS is developed and updated by the National Institute of Standards and Technology (NIST). One device that requires FIPS to be enabled to ensure CMMC compliance is the firewall.
Where to Find FortiGate Firewall Firmware for CMMC Compliance
Fortinet has specific FortiGate firewall firmware versions that are FIPS-certified. To see the latest FIPS-certified firmware, go to the NIST Cryptographic Module Validation Program search page, which is accessible here: https://csrc.nist.gov/Projects/cryptographic-module-validation-program/validated-modules/search. Under “Vendor,” type in “Fortinet” and click Search. In the search results, click on FortiOS to see the details of the certification. At the bottom, you will see the firmware version that is certified.
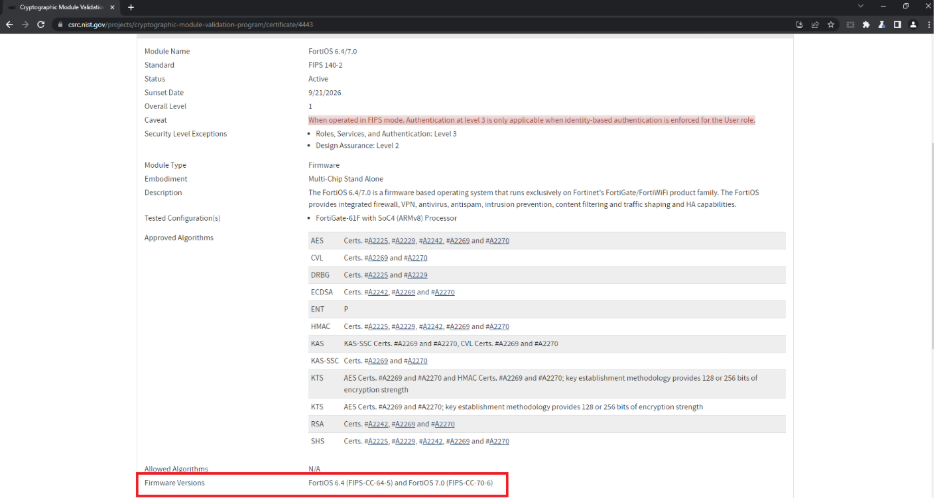
Once the firmware version is noted on the NIST website, go to the firmware download portal at https://support.fortinet.com/download/firmwareimages.aspx. Switch to the “Download” page and then browse to the FIPS-CC-Certified folder to download the firmware version corresponding to the FIPS-certified version that was noted earlier.
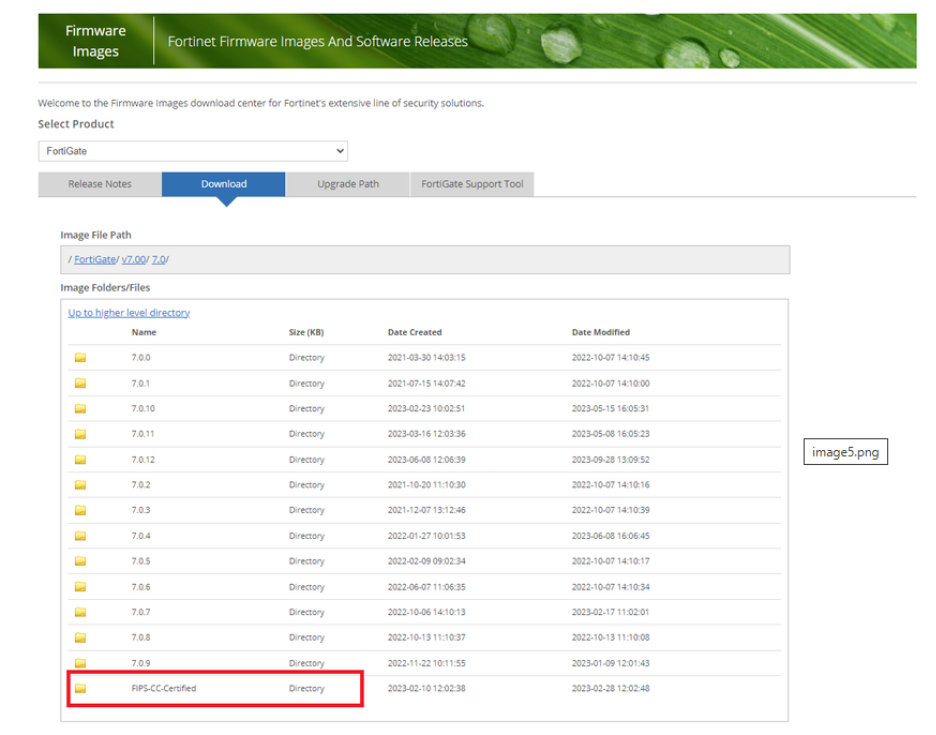
Once the firmware is downloaded, it can be installed the same way you would install other firmware versions, but the initial configuration of the firewall is different. We will discuss how to do the initial configuration of a FIPS-enabled FortiGate firewall in Part 2 of this blog post.
If you have any other questions about CMMC compliance, FIPS mode, or FortiGate firewalls please contact Sikich.




